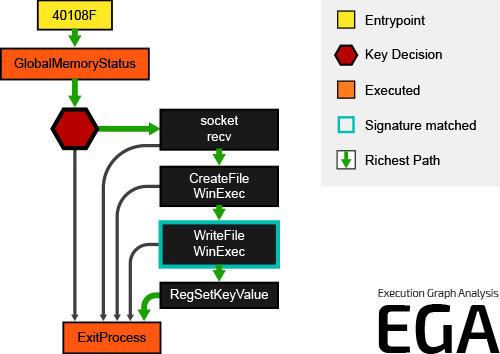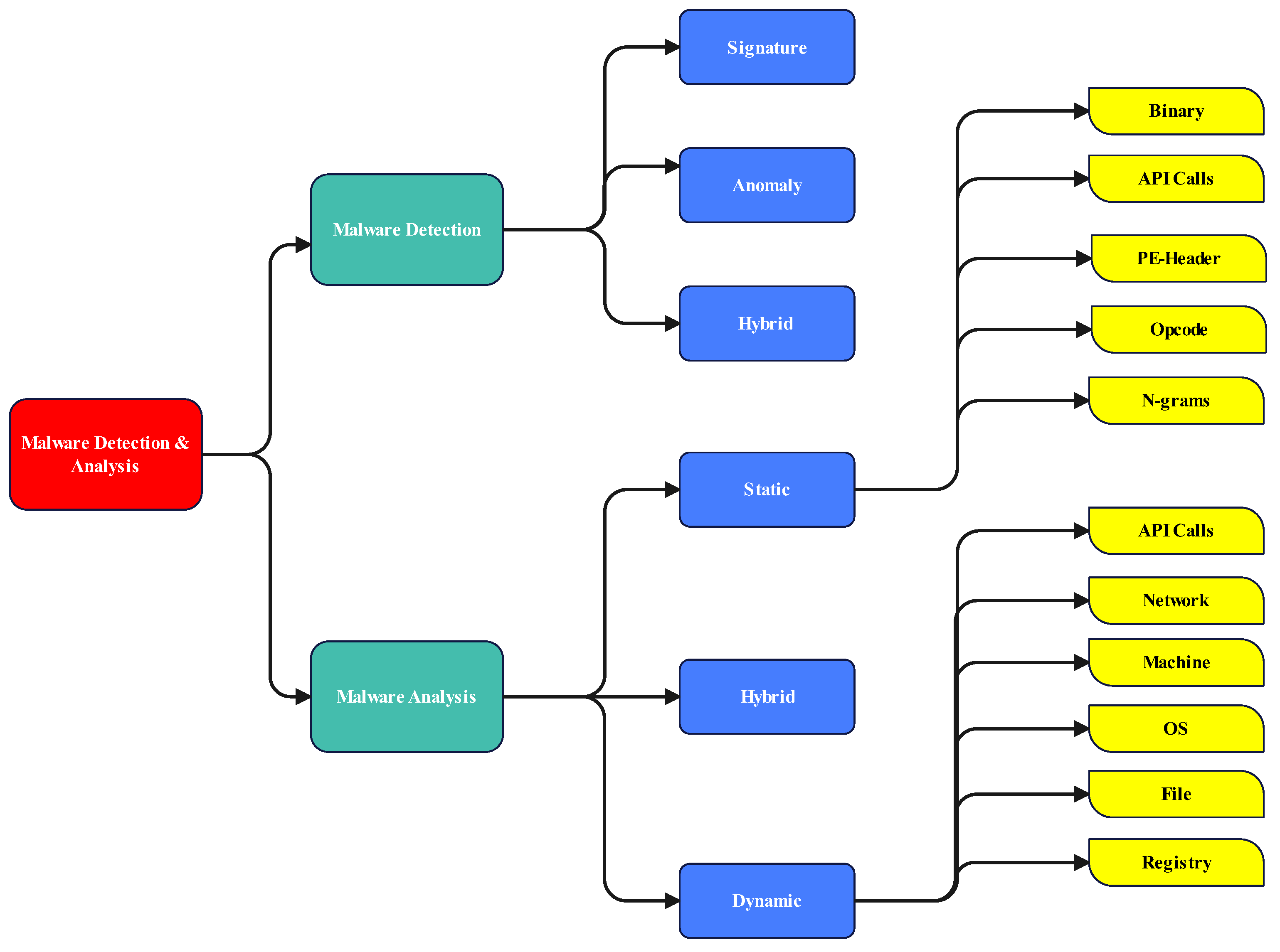
Symmetry | Free Full-Text | Artificial Intelligence-Based Malware Detection, Analysis, and Mitigation

Entropy | Free Full-Text | A Hybrid Analysis-Based Approach to Android Malware Family Classification

A malware detection system using a hybrid approach of multi-heads attention-based control flow traces and image visualization | Journal of Cloud Computing | Full Text

Hybrid Intelligent Android Malware Detection Using Evolving Support Vector Machine Based on Genetic Algorithm and Particle Swarm Optimization | Semantic Scholar
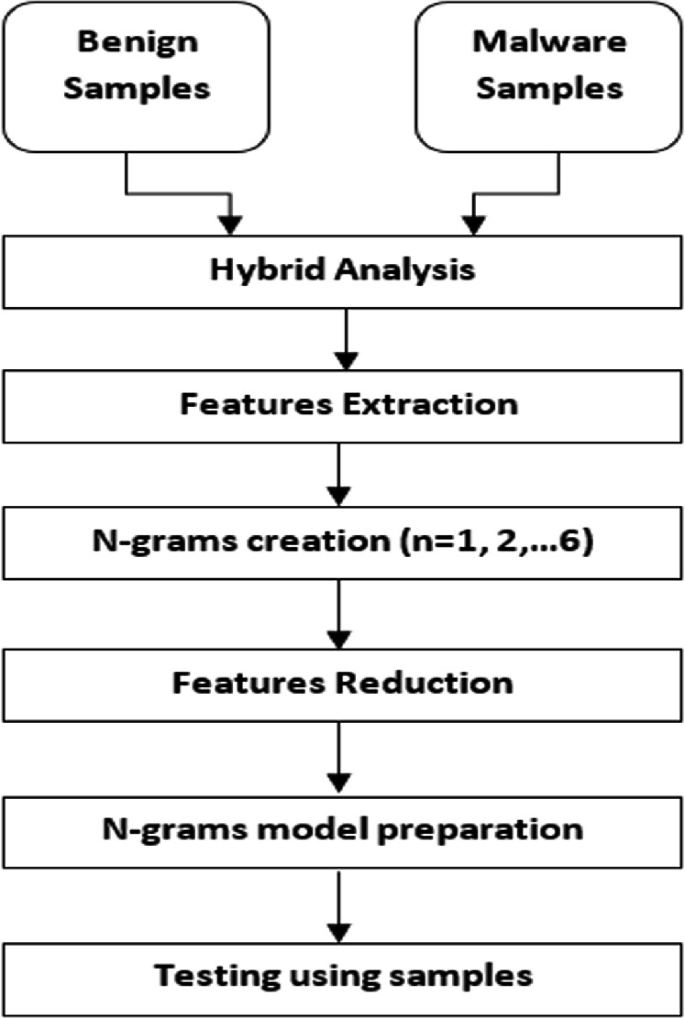
Android Malware Detection with Classification Based on Hybrid Analysis and N-gram Feature Extraction | SpringerLink
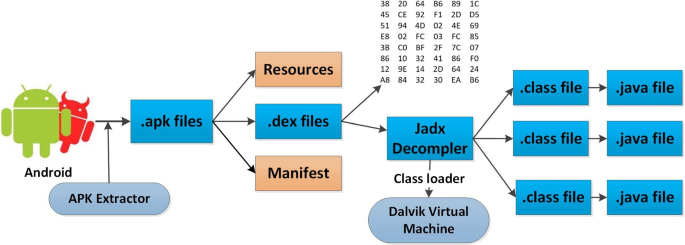
A malware detection system using a hybrid approach of multi-heads attention-based control flow traces and image visualization | Journal of Cloud Computing | Full Text

Figure 2 from Profiling mobile malware behaviour through hybrid malware analysis approach | Semantic Scholar